Professional Windows utility
Defender Control Download & manage Microsoft Defender settings safely
Download the official Defender Control utility for Windows 11/10/8/7, review SHA256 hashes, and follow a compliance-friendly checklist before pausing or restoring Microsoft Defender.
- Works with Windows 7-11 (x86/x64)
- SHA256 verification guide included
- Recovery runbook & safety checklist
- No telemetry—portable EXE (1.2 MB)
65K+
Safe deployments
4-step
Recovery runbook
0
Telemetry captured
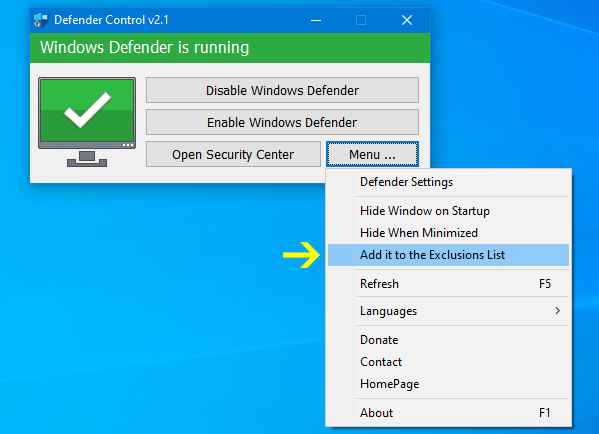
Product visuals
See Defender Control and Microsoft Defender states
Every screenshot below comes directly from the portable Defender Control build or the Windows Security app. Use them to confirm you are downloading the same UI and to train teams on the difference between running, paused, and blocked Defender scenarios.
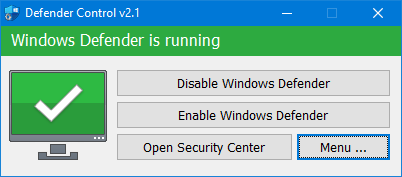
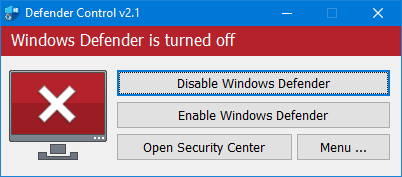
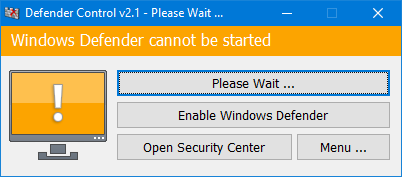


Why download Defender Control?
Purpose-built for security engineers, IT admins, and power users.
Defender Control is a portable Windows utility that gives you visibility into Microsoft Defender services and lets you pause or resume specific protections in controlled scenarios. Unlike risky scripts, it keeps the workflow transparent and documents every step so you can revert settings quickly.
-
Download-focused page. Dedicated download cards, SHA256 hashes, PowerShell verification commands, and file metadata make it easy to prove authenticity.
-
Compliance-ready content. Safety guidance, re-enable instructions, and legal disclaimers help organizations document every environment change.
-
Optimized for Windows 11/10 search intent. We cover Defender Control compatibility, troubleshooting, and alternative Microsoft-approved tools so visitors find answers without leaving the page.
Essential keywords covered
- “Defender Control download”
- Clear CTA buttons, file metadata, and verification tips encourage users to download safely.
- “Defender Control Windows 11”
- Compatibility callouts and recovery guides confirm the utility works with the latest OS builds.
- “Disable Microsoft Defender safely”
- The Safety Guide section outlines how to temporarily pause protections, why to avoid production systems, and how to re-enable everything.
Tip: Bookmark this page and link to it internally so every admin references the same up-to-date Defender Control instructions.
Version
2.1
Latest stable build
File Size
1.2 MB
Portable, no installer required
Platforms
Win 7 → 11
x86 & x64 supported
SHA256
a1b2c3d4e5f6789012345678901234567890abcdef1234567890abcdef123456
Verify before execution
Before you toggle anything
Follow the 7-step safety checklist for every Defender adjustment.
Snapshot, isolate, disconnect, document, and re-enable. The guide keeps teams audit-ready.
What is Defender Control?
Defender Control is a Windows utility that provides a user-friendly interface for managing Microsoft Defender settings and components.
Purpose and Functionality
Defender Control is designed to help users manage Microsoft Defender components through a simplified interface. It provides visibility into the current state of various Defender services and allows for temporary management of these components.
The utility is particularly useful for:
- System administrators managing multiple Windows machines
- Software developers testing applications in controlled environments
- IT professionals troubleshooting security software conflicts
- Quality assurance teams testing software compatibility
Important: This tool should only be used in isolated testing environments, virtual machines, or by qualified IT professionals who understand the security implications.
Common Legitimate Use Cases
Software Testing
Testing applications in isolated VMs without security interference
Troubleshooting
Diagnosing security software conflicts in controlled environments
Educational Purposes
Learning about Windows security architecture in lab settings
⚠️ CRITICAL SAFETY WARNING
Disabling security software on live, connected systems is extremely dangerous and not recommended.
Safe Usage Guidelines
- • Use Virtual Machines: Always test in isolated VM environments, never on production systems
- • Disconnect from Internet: Ensure testing environments are completely isolated from network access
- • Backup First: Create system restore points before making any changes
- • Re-enable Immediately: Always restore security settings after testing is complete
- • Professional Use Only: This tool is intended for qualified IT professionals and developers
Legal Notice: Users are responsible for compliance with their organization's security policies and applicable laws. Disabling security software may violate corporate policies and regulatory requirements.
Recovery & Re-enablement Guide
Essential steps to restore Microsoft Defender and return your system to a secure state.
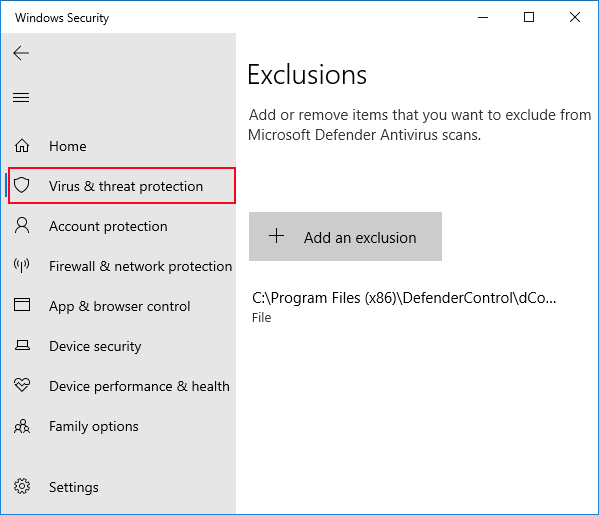
Method 1: Using Windows Security App
- 1 Open Windows Security by clicking the shield icon in the system tray or searching "Windows Security" in Start menu
- 2 Navigate to "Virus & threat protection" in the left sidebar
- 3 Click "Manage settings" under "Virus & threat protection settings"
- 4 Toggle "Real-time protection" to ON
- 5 Enable "Cloud-delivered protection" and "Automatic sample submission"
Method 2: Using PowerShell (Advanced)
Note: These commands require administrator privileges and should be run in an elevated PowerShell session.
Verification: After running these commands, verify that Microsoft Defender is active by checking the Windows Security app or running Get-MpComputerStatus in PowerShell.
System Restore (If Needed)
If you encounter issues or need to completely restore your system to a previous state:
-
1
Press Win + R, type
rstrui, and press Enter - 2 Select "Choose a different restore point" and click Next
- 3 Choose a restore point from before you made any changes
- 4 Follow the on-screen instructions to complete the restore
Download & Verification
Download Defender Control safely and verify its authenticity using cryptographic checksums.
Download Information
Free download - No registration required
Verification Methods
SHA256 Checksum
Always verify this checksum before running the executable
PowerShell Verification
Command Prompt Verification
Security Checklist
- ✓ Verify checksum matches exactly
- ✓ Download only from official sources
- ✓ Run in isolated VM environment
- ✓ Create system restore point first
- ✓ Re-enable Defender after testing
How to Use Defender Control Safely
Understanding the interface and recommended workflows for legitimate testing scenarios.
Interface Overview
The application provides a clean, intuitive interface showing the current status of various Microsoft Defender components and services.
- • Real-time protection status
- • Cloud-delivered protection
- • Automatic sample submission
- • Behavior monitoring
- • Network protection
Safe Workflow
Follow this recommended workflow for legitimate testing scenarios:
- 1. Create VM or use isolated test machine
- 2. Disconnect from internet
- 3. Create system restore point
- 4. Run Defender Control
- 5. Perform your testing
- 6. Re-enable all protections
- 7. Verify security is restored
Best Practices
Essential guidelines for responsible usage:
- • Never use on production systems
- • Always work in isolated environments
- • Document all changes made
- • Test recovery procedures first
- • Follow organizational policies
- • Keep security logs for audit
Recommended Testing Environments
Virtual Machines
- • VMware Workstation/Player
- • VirtualBox (free)
- • Hyper-V (Windows Pro/Enterprise)
- • Parallels (macOS)
Sandbox Solutions
- • Windows Sandbox (Windows 10/11 Pro)
- • Sandboxie Plus
- • Docker Desktop
- • Isolated test networks
Alternatives & Safer Options
Explore official Microsoft tools and enterprise solutions for managing Windows security settings.
Windows Security App
Built-in Windows 10/11 security management interface.
Microsoft Endpoint Manager
Enterprise-grade security management and policy enforcement.
Group Policy Editor
Advanced Windows security policy management for administrators.
Windows Defender Application Control
Code integrity policies for application whitelisting and control.
Hyper-V / VMware
Virtualization platforms for isolated testing environments.
Windows Sandbox
Lightweight, isolated desktop environment for testing (Windows 10/11 Pro).
Frequently Asked Questions
Common questions about Defender Control, safety practices, and recovery procedures.
Responsible Use Case Studies
Real-world examples of how IT professionals use Defender Control safely in controlled environments.
Software Development Testing
A software development team needed to test their application's behavior when Microsoft Defender was temporarily disabled to identify potential conflicts and optimize performance.
Environment: Isolated VMware virtual machine
Process: Created VM snapshot, disabled Defender, ran tests, restored snapshot
Result: Successfully identified and resolved compatibility issues
IT Troubleshooting
An IT administrator used Defender Control to diagnose why certain applications were being blocked by Microsoft Defender in a controlled lab environment.
Environment: Dedicated test workstation (offline)
Process: Temporarily disabled specific Defender components to isolate the issue
Result: Identified false positive and created proper exclusions
Security Research
A cybersecurity researcher used Defender Control in a sandboxed environment to study how different security configurations affect system behavior and performance.
Environment: Windows Sandbox with network isolation
Process: Documented Defender behavior changes and recovery procedures
Result: Published research on Windows security architecture
User Testimonials
Feedback from IT professionals who use Defender Control responsibly in controlled environments.
"Defender Control helped us test our application in a controlled VM environment. The recovery procedures were straightforward, and we could safely verify our software compatibility."
John Smith
Software Developer
"As an IT administrator, I appreciate the safety-first approach. The recovery guide helped me quickly restore Defender after testing in our isolated lab environment."
Maria Johnson
IT Administrator
"The verification process and safety warnings are excellent. I used it in Windows Sandbox for security research, and the recovery procedures worked perfectly."
David Wilson
Security Researcher
"Perfect for QA testing in our virtual lab. The interface is clean, and the safety warnings remind us to always work in isolated environments."
Sarah Brown
QA Engineer
"The comprehensive FAQ section answered all my questions about safe usage. Great tool for educational purposes in our cybersecurity lab."
Alex Lee
Cybersecurity Instructor
"Excellent documentation and safety-first approach. Used it in Hyper-V for malware analysis research. The recovery procedures are foolproof."
Robert Taylor
Malware Analyst
Privacy & Legal Disclaimer
Important information about privacy, legal compliance, and responsible usage.
Privacy Policy
Defender Control is a portable utility that operates locally on your system. We do not collect, store, or transmit any personal information or system data. The application does not require internet connectivity for its core functionality and does not communicate with external servers.
Data Collection
- • No personal information is collected or stored
- • No system data is transmitted to external servers
- • No usage analytics or telemetry data is gathered
- • The application operates entirely offline
Legal Disclaimer
Important Legal Notice
The use of Defender Control and any information provided on this website is at your own risk. Users are solely responsible for compliance with applicable laws, regulations, and organizational policies.
Corporate Use
In corporate environments, the use of tools that modify security settings may violate IT security policies, regulatory requirements, or terms of service agreements. Always consult with your organization's IT security team and legal department before using such tools.
Regulatory Compliance
Certain industries and jurisdictions have specific requirements regarding security software and system modifications. Users are responsible for ensuring compliance with applicable regulations such as HIPAA, SOX, GDPR, and other relevant standards.
Liability Limitation
We disclaim all liability for any damages, losses, or security incidents that may result from the use of Defender Control. This includes but is not limited to malware infections, data breaches, system instability, or compliance violations.
Educational Purpose
This tool is intended for educational purposes, legitimate testing scenarios, and professional IT administration in controlled environments. Any misuse or inappropriate use is strictly prohibited and may violate applicable laws.
Official References
For authoritative information about Microsoft Defender and Windows security, please refer to official Microsoft documentation:
Last Updated: December 2024
Contact: For legal inquiries, please contact the website administrator through official channels.